Have you jumped on the cryptocurrency bandwagon yet? Either buying your own with fiat money, or dedicating some hardware to mine it?
This article shows how you may have been contributing some computing resource to mine crypto recently without your conset. A script by a company call CoinHive has been making an appearance on various websites, using the visitors browsers to mine cryptocurrencies.
End user computers are one resource for hackers to exploit, and if you’re not careful your virtual machines running in the cloud could be compromised by hackers to mine crypto.
The other month a client contacted me about a warning in their Google Cloud console, that there was some unauthorised usage in their account.
At first I thought it was something they had done with their account, but when had a quick look at the Compute Engine instances it became very clear what the issue was.
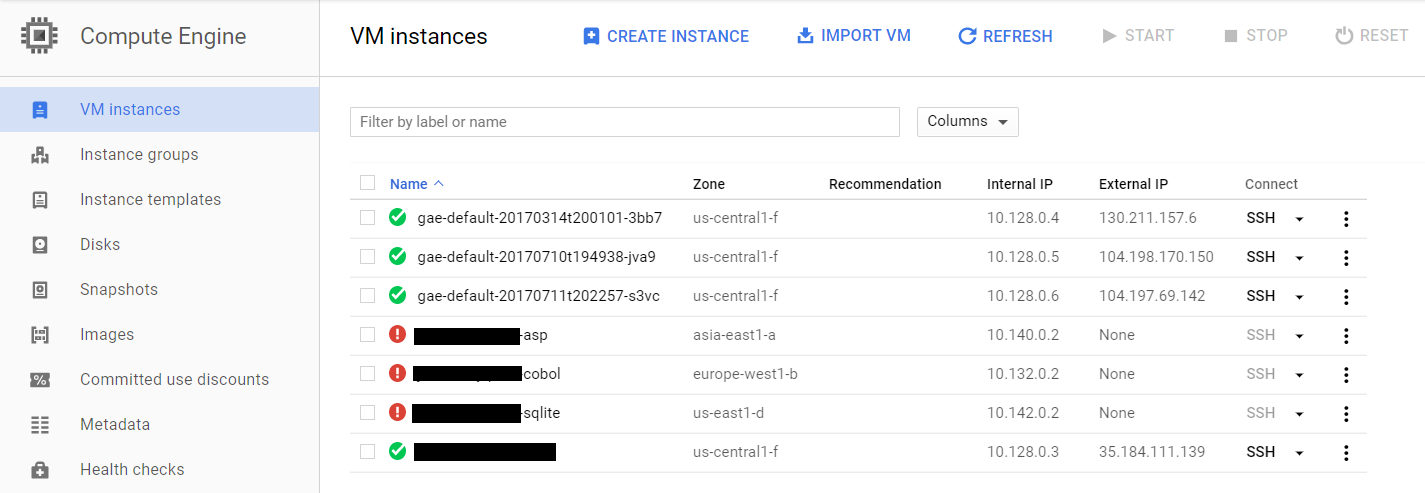
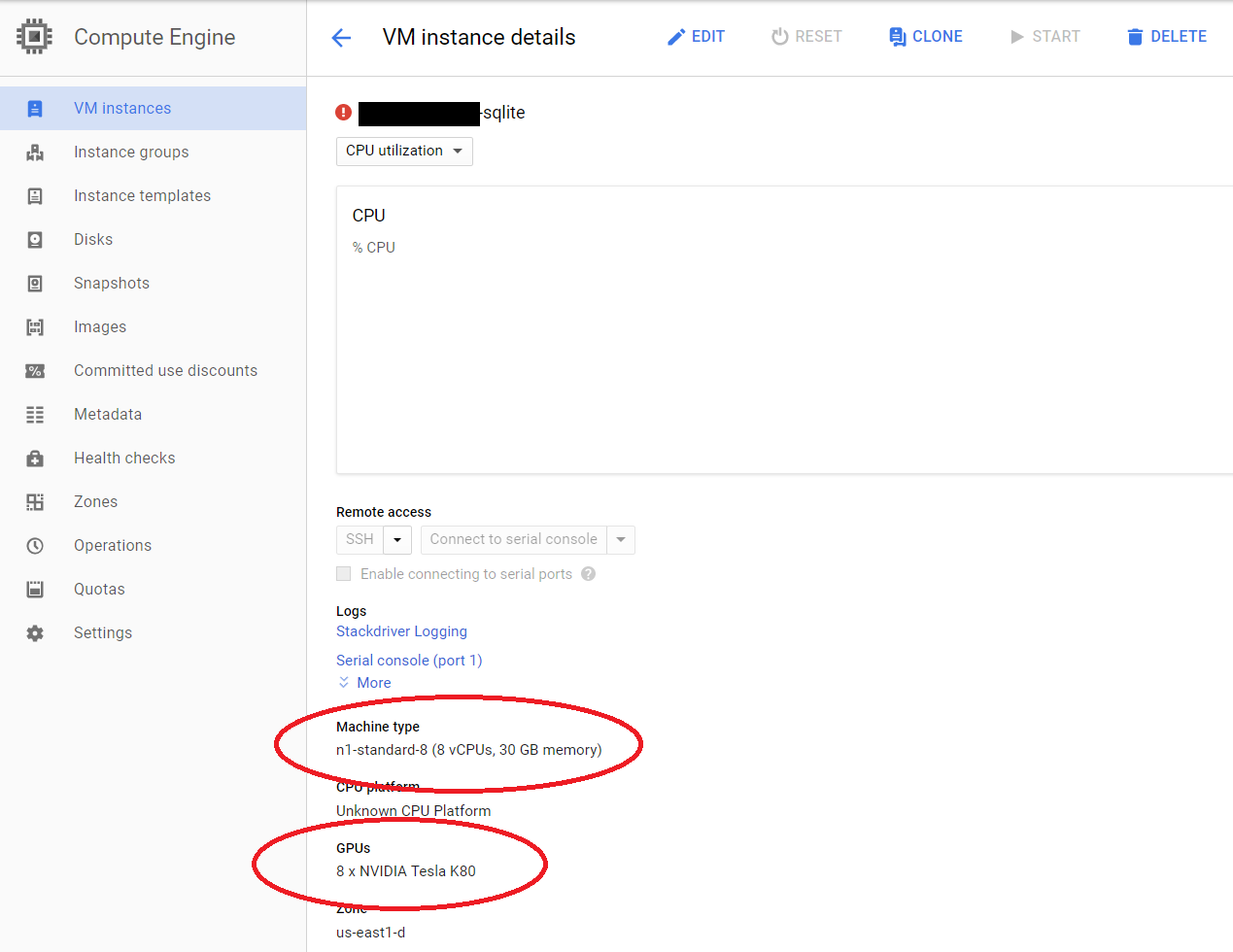
3 unexpected VM instances were running, and not little 1 CPU VM’s that the Node.js web servers run on. These were 32 vCPU instances with 8 NVidia GPU attached each, the maximum amount of GPU’s possible per VM. This was on track to make their monthly cloud costs 10x their usual amount.
Not surprisingly if you take time to read the Google Cloud terms and conditions when you sign up for their free trial you’ll notice that mining crypto is not allowed for the free credits.
My strong guess is these machines were mining crypto, whether Ethereum or others favoured my hacker miners. I doubt they were using the GPU’s to run physics simulations. Whether it was a 3rd party/hacker who obtained the service account key which would have enabled them to create the VM instances or one of their internal staff we won’t know.
The service account key which was being used was immediately revoked, and the permissions granted to the developers reviewed to reduce the roles granted where possible.
This goes to show how viligant you need to be with your security and monitoring your cloud resources, lest you become an unwitting miner.